Using Session Host Update in Azure Virtual Desktop.
Using Session Host Update in Azure Virtual Desktop.
Hello Welcome Back! In this blog i want to talk about updating sessionhosts configuration in Azure Virtual Desktop (AVD). Microsoft continuously improves the platform, and the Session Host Update feature, currently in preview, is one of the latest innovations. This post will explore what Session Host Update can do for your organization, how to use it, how to set it up, its limitations, and known issues.

What is Session Host Update exactly and why you want to use it?
Managing and updating session hosts in a host pool can be time-consuming and sensitive for mistakes. Traditionally, updating VM configurations required manual effort, increasing the risk of inconsistencies. Session Host Update streamlines this process by allowing you to:
- Standardize Host Configurations: Ensure all session hosts use the same OS image, disk type, and VM size.
- Host Updates: Replace existing session hosts with new ones configured to the latest specifications, all without disrupting your users.
- Reduce Maintenance Time: Automate repetitive tasks like domain joins and applying custom scripts.
In short, this feature helps your IT department to focus on other strategic tasks while ensuring a consistent and reliable user experience.
Which options you have when using this functionality
Here is a an overview about the possibilities when you want to use this resource:
- Virtual machine image
- Virtual machine size
- Virtual machine disk type
- Virtual machine security type
- Active Directory domain join credentials
- Microsoft Intune enrollment
- Local administrator credentials
- Run a custom configuration PowerShell script
So the cool thing about this option is that you don't need to manually go over every machine, when you for example want to change the SKU. You can configure this in the session hosts update and it will do it for you in a plannned time and date.
Things to know beforehand?
Session Host Update simplifies the update process with an automated workflow that handles every aspect of updating session hosts in a host pool. When you are going to use this you need to think about it beforehand, because some things will be done differently.
- You need to check the option when creating the hostpool when creating the hostpool, you need to check the below option you cannot do it after:
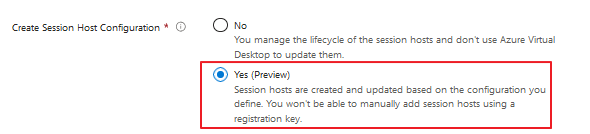
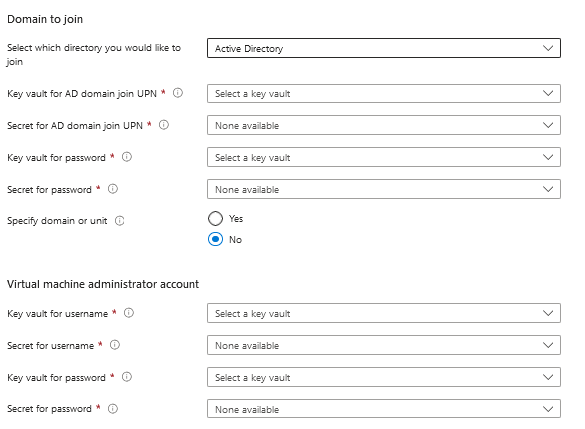
- There are more dependencies because you need to join the hosts to a domain you need to use secrets, that are stored in a Key-vault this is an example of an extra resource that is needed when setting this up. There are a view RBAC roles need to be added when you are using this new feature.
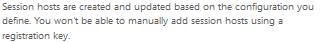
- If you use this option you cannot mannually add sessionhost anymore because you choose to update using the schedule host configuration, you cannot add sessionhosts manually in that hostpool, it will not generate an registration token anymore.
Known Limitations
While powerful, the Session Host Update feature does have some limitations:
- Preview Status: The feature is in preview and not covered by service-level agreements, if you are going to use this process please test it carefully in test environment.
- One Operation at a Time: Only one update process can run or be scheduled per host pool.
- Quota: Keep in mind that you need to monitor your quota's if you run out of quota the update process will fail.
- Details: When the update process is running you can see not that many details, you need to trust the process and check the activity log or azure monitor for activity.
What are the prerequisites
Below i have summed up a list of prerquisites you need to take account of when you want to use this for your hostpoold:
An hostpool "pooled" with all session hosts located in the same Azure region and **resource group "personal" hostpools are not supported.
Image must be supported for Azure Virtual Desktop an must match the image generation of the machine virtual machine.
If using Trusted launch virtual machines or Confidential virtual machines, the image must be for Generation 2 virtual machines.
The image can come from: Azure Marketplace, Azure Compute Gallery or a Managed image.
Remove any resource locks on session hosts or the resource group containing them.
Assign the Azure Virtual Desktop service principal (WVD) the following roles for the host pools and session hosts:
- Desktop Virtualization Virtual Machine Contributor
More information on assigning Azure RBAC roles.
- Desktop Virtualization Virtual Machine Contributor
Ensure the Azure account used for configuration has these built-in roles (or equivalent custom roles):
Resource Type Built-in Azure RBAC Role Scope Host pool Desktop Virtualization Host Pool Contributor Resource group or subscription Application group Desktop Virtualization Application Group Contributor Resource group or subscription Session hosts Virtual Machine Contributor Resource group or subscription Session hosts must be joined to an Active Directory domain, Microsoft Entra ID join and Microsoft Entra Hybrid domain join is not supported.
For Microsoft Entra Domain Services (Azure AD DS), you must be a member of the AAD DC Administrators group.
For Active Directory Domain Services (AD DS), the account must have elevated permissions due to the reuse of the existing computer object. Permissions required on the Organizational Unit (OU) include:
| Name | Type | Applies to |
|---|---|---|
| Reset password | Allow | Descendant Computer objects |
| Validated write to DNS host name | Allow | Descendant Computer objects |
| Validated write to service principal name | Allow | Descendant Computer objects |
| Read account restrictions | Allow | Descendant Computer objects |
| Write account restrictions | Allow | Descendant Computer objects |
The user account joining the session host must, be the creator of the existing computer account or be a member of the Domain Administrators security group.
Apply the Group Policy setting:
Domain controller: Allow computer account re-use during domain join`.an Key-Vault containing secrets for the virtual machine local administrator account credentials and domain join account credentials if of course you want to join them to a domain.
The Key Vault must Allow Azure Resource Manager for template deployment, provide read access for the Azure Virtual Desktop service principal (WVD):
Using Azure RBAC: Assign the "*Key Vault Secrets User" role to Azure Virtual Desktop service principal (WVD).
Using an access policy: Assign the "Get secret" permission to Azure Virtual Desktop service principal (WVD).
Azure Virtual Desktop service principal (WVD) also needs access to virtual network and azure image gallery.
The URL for any custom PowerShell scripts specified in the session host configuration must be resolvable from the public internet.
If using Azure PowerShell locally, ensure you have the Az.DesktopVirtualization PowerShell module installed. Installation instructions. Install the preview version of the Az.DesktopVirtualization module (version 5.3.0 or later).
Let's set this up!
- So first let's create a keyvault, i assume you know how to do this, but if not, you can find the steps on this Microsoft Learn page, you will need this key vault for storing the secrets. Keep in mind that you need to set the Access Policy or the RBAC permissions for the Windows Virtual Desktop give it the "Key Vault Secrets User" when you use RBAC or use "Get Secret" when using access policies.
- Store the secrets in the key-vault you can do this manually trough the portal but you can also use powershell for that you can read how to do it in the Microsoft Learn docs.
In this demo I created 4 secrets containing: DomainAdmin, DomainPassword, LocalAdmin, LocalPassword.

- You also need to check the checkbox "Azure Resoure Manager for Template deployment" under the "acces configuration":

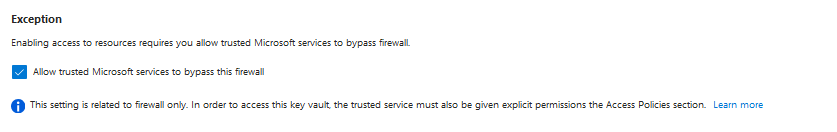
And bypass Azure Services:
- I gave the "Windows Virtual Desktop" the necessary RBAC permissions on the resource group where my hostpool and session hosts will be deployed.

- I gave the "Windows Virtual Desktop" the necessary RBAC permissions on the Azure Compute Gallery to read the image where the image is stored.

- I gave the "Windows Virtual Desktop" the necessary RBAC permissions on the Virtual network where the session hosts needs to be deployed in.

- In the Azure Virtual Desktop section I have created the hostpool, select the pooled type and chose for the Session Host Configuration "yes".
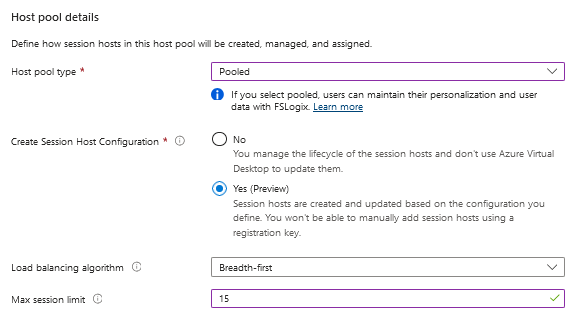
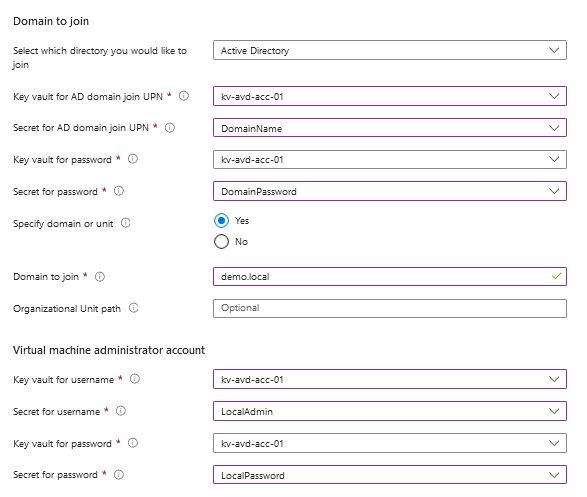
- I chose my preferred settings which image, security, network and availability. In the below section the options to domainjoin, and Virtual Machine local admin accounts are new and needed, I have selected the key-vault where the secrets are stored in:
- I hav selected the workspace and created the hostpool.
It will now set-up and deploy the session-hosts as we have configured, this will take a while, depending on how many machines you have choosed.
What is next?
When the deployment is finished you will see some extra options when selecting the hostpool, we can view or edit the current configuration by clicking "Manage session host configuration" or we can choose "Manage session hosts update" so we can plan a new update.
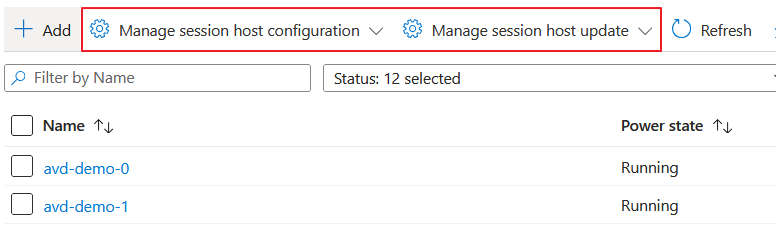
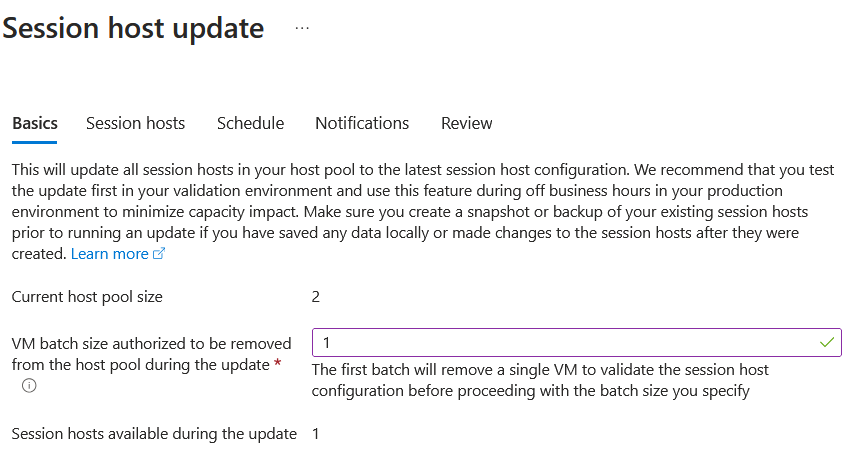
- let's plan a new update, i want to change the SKU size, click on "manage session hosts update" and choose "new". In the first you will see there are 2 session hosts and there will be 2 available during the update. I will choose 1 for the batch size because I want one session host available during the update, more information can be found here.
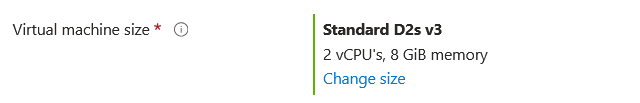
- In the next window I will only change the SKU:
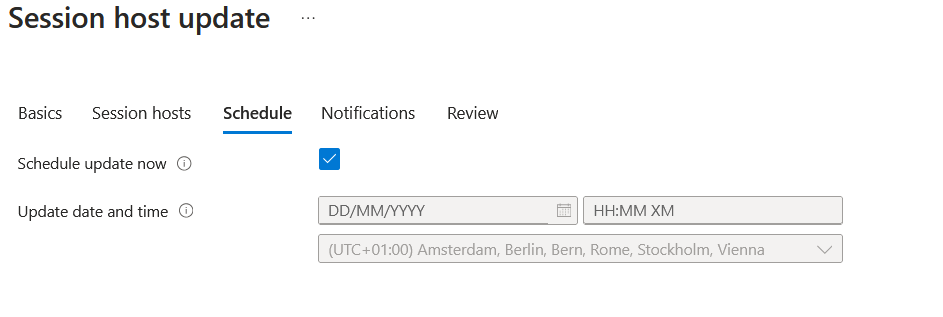
- Under the schedule section, I will choose for "update now" but you could also plan this for a later time, if you want.
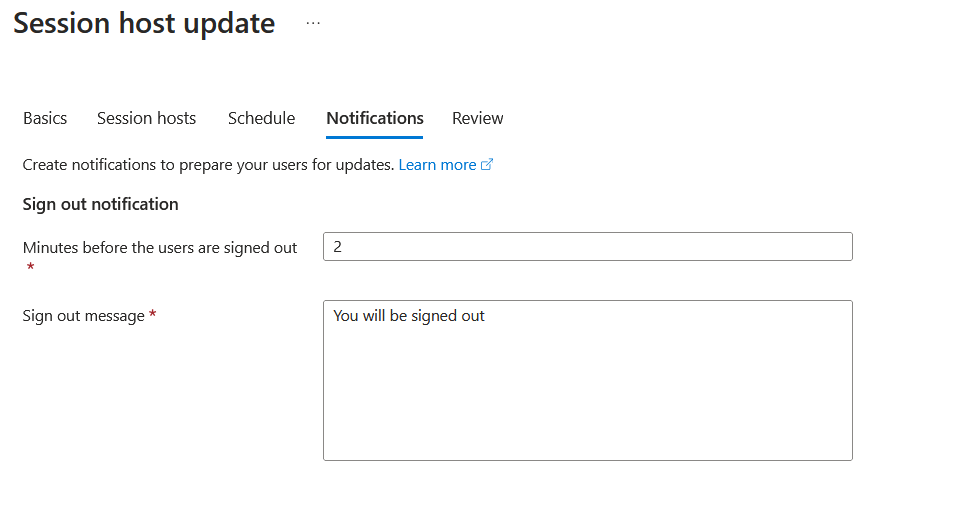
- In the last step you could notify any users that are logged in if this is needed, review and create the update.
It will now validate the configuration and will tell you the status, in the overview of the hostpool.
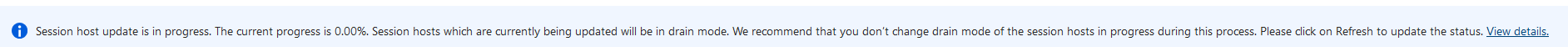
You will also see that session hosts will have the deallocating state when updating is applied on the session host.

Drain mode is automatically being enabled when updating is started for the session host.
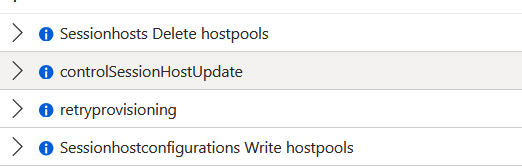
If you want to monitor the proces, you can check the activity log in the hostpool.
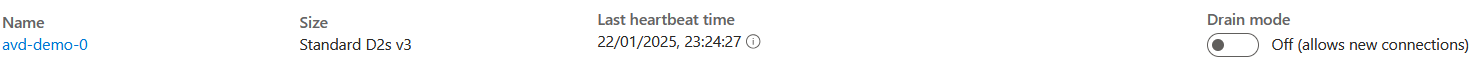
The machine(s) will be deleted and added back in the hostpool as you can see, with the same name, drain mode is already disabled and the new sku is being set.
So changing the sku is just one possibility, but there are a lot more, test it's potential in your test environment!.
Conclusion
Session Host Update is a significant leap forward for managing session hosts in Azure Virtual Desktop. By automating and standardizing updates, it reduces administrative overhead and ensures your environment remains reliable and consistent. Although it’s currently in preview, its potential to simplify host management makes it worth exploring. Therefore it will be good to first use and test this in your test environment before setting this up in production.
Thanks for reading my blog and see you next time!